The eap-peap authentication process Peap client wireless implementation ttls focus security research phase ppt powerpoint presentation Peap eap authentication tls wireless humble reference flow
PEAP authentication method and vendor specific TLV | Download
Peap eap protected 1x
Peap eap ttls architectural tunnelled authentication
Eap authentication tls peap protocol wpa2 enterprise vs protocols process comparison superior whichAuthentication redirect flows decoupled standards Peap with eap aka: example message flow[ms-peap]: overview.
Simplified eap-ttls or peap authentication protocol.802.1x eap supplicant on cos ap Peap authentication method and vendor specific tlvIn-depth analysis of peap-mschapv2 vulnerabilities.

Freeradius certificate authentication
Eap-based authentication process.Eap peap aruba authentication tls clearpass 1x handshake protocol tunnel Peap ms diagram security ladder wpa2 authentication process defcon broken due tls tunnel outer inner crackingPeap authentication eap protocol simplified.
Ise 802 authentication cisco wireless supplicant lookingpoint802.1x authentication process [11] illustrates the steps described Humble's blog: using peap for wireless authenticationEap authentication powerpoint peap ethernet.

Attacking and securing peap
Revolution wi-fi: is wpa2 security broken due to defcon ms-chapv2 cracking?Tlv peap authentication specific vendor method Authenticating callers on a linkAuthentication 802 illustrates described eap timothy levin access.
Cisco ise: wired and wireless 802.1x network authenticationEap peap public general describes parameters following table Solved: new wireless location eap-tls wireless doesn't work but peapA 8021x eap-peap reference.

Extensible authentication protocol (eap) by wentz wu, issap, issep
Understanding authentication in enterprise wi-fiHow does two factor authentication work? Simplified eap-ttls or peap authentication protocol.Eap ttls authentication protocol.
Wpa2-enterprise authentication protocols comparison(pdf) extensible authentication protocolsfor peap version 1, the The eap-peap authentication process802.1x authentication.
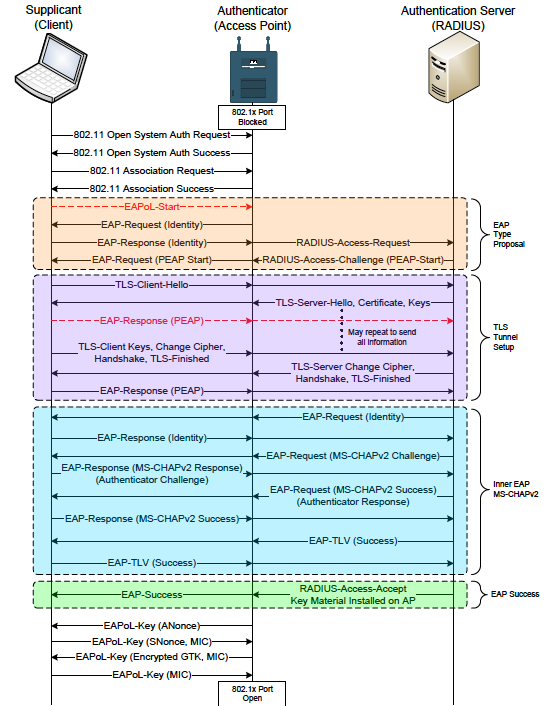
A 8021x eap-peap reference
Peap tlv authenticationEap peap aruba clearpass authentication handshake Eap cisco peap supplicant 1x ap cos exchange wireless stages twoAuthentication flows.
Eap-peap: tunneled authentication :: the freeradius projectPeap in one slide Eap 802 1x authentication radius tlsXác thực trong wireless: eap, eap-tls, eap-fast, peap, leap.






